DDoS/DoS attacks: experience-based insight. Part I
Today everyone knows about DDoS/DoS attacks. The buzz has long spread beyond security testing and is now everywhere: on the internet, TV, etc. You don’t have to be an experienced user to face the consequences of these attacks, when you visit, for example, a favorite news portal and see the “service is unavailable” message, here it is – the DDoS/DoS attack.
Even knowing what the letters DDoS/DoS stand for, do you understand what they mean? DoS means Denial of Service, which is a malicious activity aimed at a web-site to make it unavailable for legitimate users. DDoS means Distributed Denial of Service, which is an attack performed by several computers.
The most often motives for carrying out DDoS/DoS attacks are:
- Political protest
- Unfair competition
- Blackmailing
- Personal issues
The first DoS attack was registered in September 1996. A few days after the first attack – on September 19th – Carnegie Mellon University computer team of fast response to information security incidents published a brochure about DDoS/DoS attacks. In 1999-2000 when the largest portals like Ebay, Amazon and Yahoo couldn’t handle the attacks the information about them spread around the world. Several years later in 2010 DDoS attacks became notorious again. Hackers started applying them for political protests and attacked the biggest e-commerce systems, like Paypal, Visa and MasteCard. Recently attacks have become more powerful, for example, in 2013 hackers performed a 300 Gbps attack, while in 2014 they reached a record of 400 Gbps.
DoS attack: behind the scenes
Today all attacks can be divided into three big categories depending on the target:
- Server network connection attacks
- Server CPU time attacks
- Server memory attacks
Server’s network connection attacks are aimed at server bandwidth. Hackers generate a huge stream of spurious traffic towards the goals, applying botnet or vulnerable internet servers. The attack can be compared with a traffic jam with stuck ambulance; ambulance here means connections of legitimate clients. On the scheme below you can see how the attacks with vulnerable DNS servers are performed.
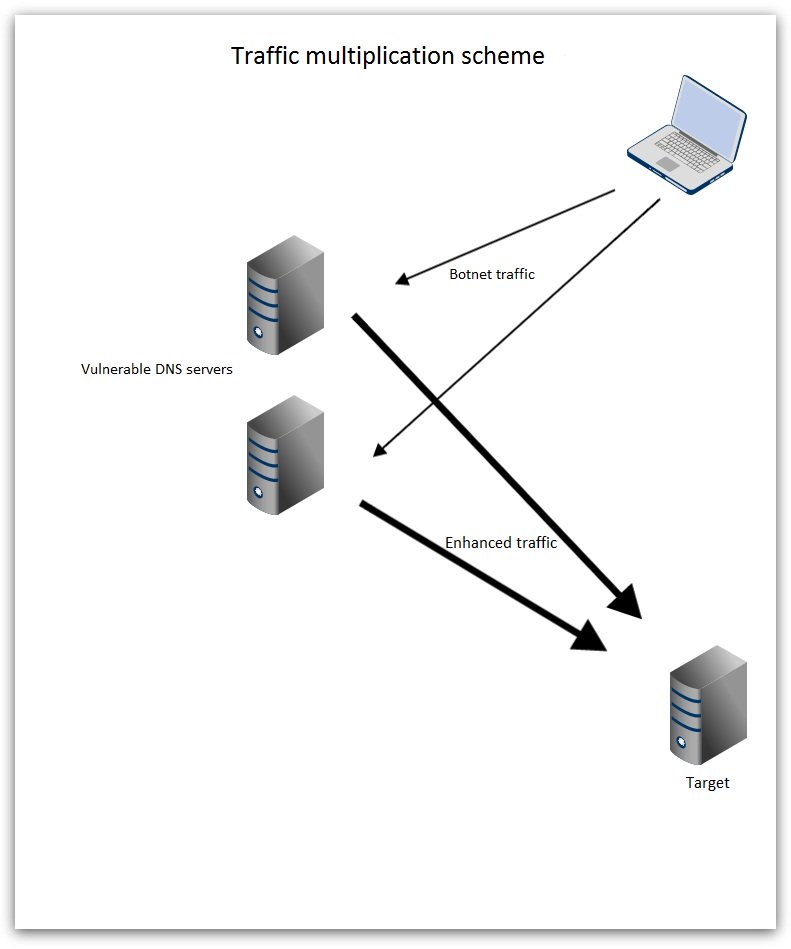
From the technical viewpoint channel attacks are very difficult. They shouldn’t run for a long period, otherwise they can harm the hacker’s system itself. Protection against these attacks is very pricey. A company has to buy expensive equipment to detect and block the attacks, or it addresses a 3rd party security provider.
Still, users should understand that this kind of attacks cannot be aimed at a blog, because the cost of the attack performance and the result are not equal.
In the next blog post we’ll cover the topics of server CPU time and server memory attacks.