
Cybersecurity: Top 5 questions to ask a QA vendor
While moving to an online environment and introducing technologies, companies face poorly secured systems. This is where cyberattacks become those of the most pressing issues, making businesses vulnerable. The price of data breach fixing will reach $10.5 trillion by 2025.
What do businesses undertake to avoid taking on high costs?
It depends. Some hire in-house cybersecurity specialists while others are looking for support from independent vendors — Software Testing Companies.
Let’s imagine you’ve picked the last option.
Here are the top 5 questions to ask your QA provider to ensure they will help launch faultless and attack-proof IT solutions.
Question #1. “What cybersecurity testing approaches and methodologies do you apply?”
Are you using penetration testing? Right, being one of the up-to-date cybersecurity approaches, it helps simulate hackers’ behavior while identifying the software bottlenecks and mitigating the risk of cyberattacks.
What more? “DevSecOps, of course.” Good. It allows QA engineers to reveal the software’s vulnerabilities at the early development stages, eliminate loopholes, and prevent the system from exploiting by cybercriminals.
Once you have asked what methodologies a QA vendor applies, you will understand what the supplier implements to achieve increased IT product security, reduced QA costs, fixed leaks.
It’s no more necessary to explain that preventing both minor and major attacks assist in avoiding damaged reputation, compromised customer data as well as financial loss.
Question #2. “Do you have a cyber incident response plan?”
They say forewarned is forearmed, so it’s a good practice to think about a response plan in advance and create some actions in case of an emergency to react quickly to malicious usage.
In line with every possible cybercrime type and level, QA providers develop multiple scenarios to minimize the risks of exploiting the software.
In 2020, Interpol’s private sector partners mentioned that the top 4 cyberattacks related to uncertainty provoked by COVID-19 are phishing, malware, malicious domains, and fake news, resulting in the breakdown of large corporations as well as millions spent to restore them fully.
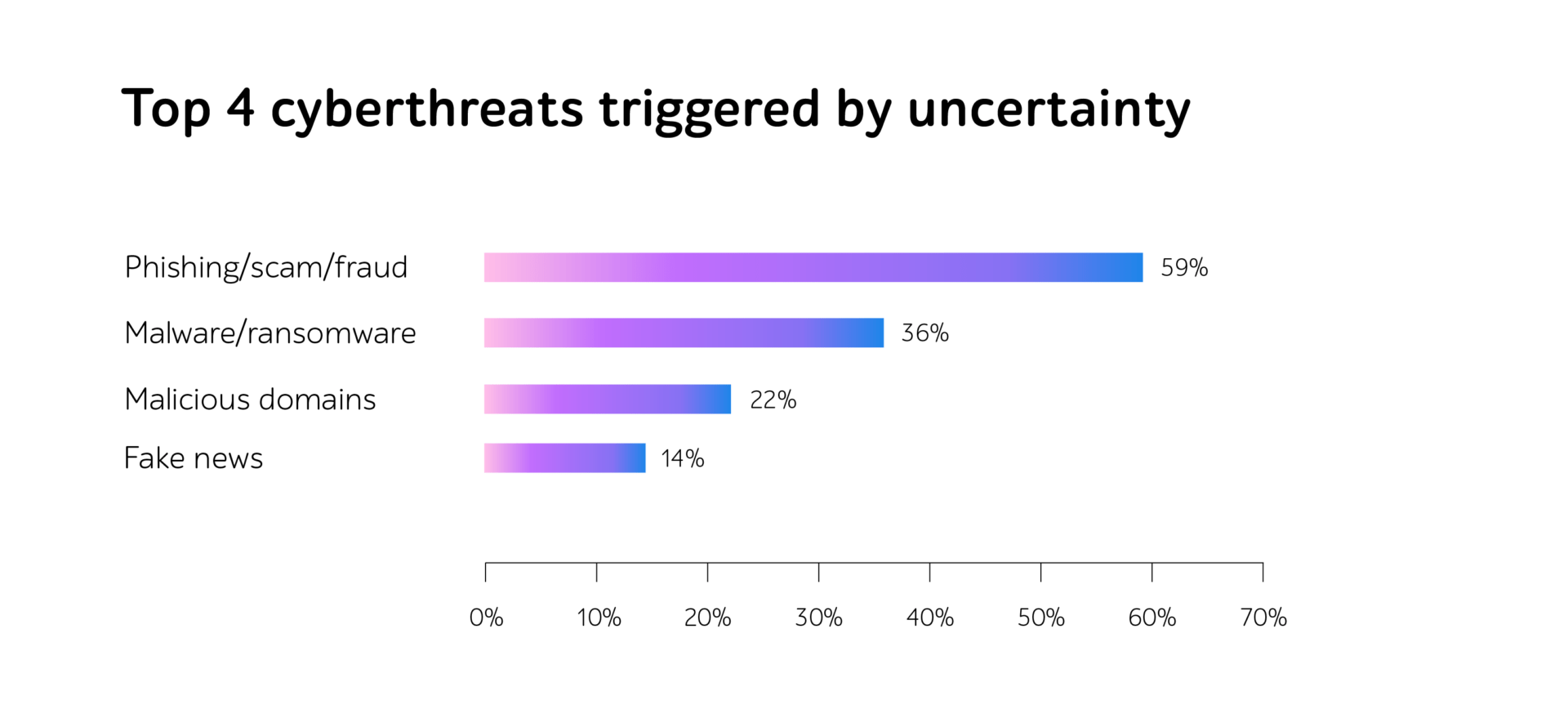
Source: www.interpol.int
Cyberattacks are becoming more sophisticated requiring new testing approaches to keep up with the pace of hackers. Make sure the QA provider considers sudden cyber incidents to timely dodge them by introducing continuous security monitoring approach paying attention to trends.
Question #3. “Do you ensure software compliance with the global safety standards?”
Working with clients’ sensitive information, range of IT products should comply with global cybersecurity standards (ISO/IEC 27001, PCI DSS, HIPAA, and others). A big deal, as they contribute to:
- Understanding risk significance and its impact on the system
- Eliminating data transmission
- Monitoring suspicious activity and preventing it.
While asking this question, more details on cross-domain expertise help understand which spheres a QA vendor has already worked in.
By ensuring the app’s compliance with standards, the provider facilitates an IT solution safety as well as customers’ protection from all types of harm, including identity theft.
Question #4. “Do you have an internal security policy?”
Clients do trust companies with a well-tuned security policy that reflects:
- Data protection standards
- Assessment of business risks
- Resources and devices used in the workflow
- Rules for non-disclosing third-party information
- Guidelines on how to establish information security for the enterprises under national and international regulations
- And more.
Hackers regularly develop new ways to penetrate the system, which requires a strengthened security policy. If employees don’t meet the safety regulations accepted within the organization, this can aggravate the situation and give cybercriminals an advantage. That is why a credible QA provider has a policy that all specialists follow to avoid data compromise and its leakage.
Sometimes cybercriminals attempt to steal data not by hacking software but by tricking the organization staff. To address similar problems, some companies develop policies to test their employees for alertness (e.g., by introducing phishing).
Question #5. “Do you educate your employees on cybersecurity issues?”
Sometimes, data breaches occur as a result of human errors (lack of expertise, untimely updating, etc.). But the consequences of cybercrimes rapidly spread across intersecting parties while triggering the spillover effect. In 2020, the Federal Reserve Bank of New York claimed that the cyberattack on any of the five most active banks affects 38% of the network because of their interconnectivity.
Providing employees with additional training helps reinforce their cybersecurity knowledge, learn how to correctly apply innovations related to the cyber environment, improve company awareness of internal security policy updates, etc.
Well-prepared cybersecurity testing specialists are assuredly adept at implementing best practices to address cybercrime issues. This can be a five-step testing cycle:
- Detecting cyber penetrations — to gain customers’ trust and ensure secure software.
- Identifying risks — to evaluate possible methods of threat elimination.
- Protecting software — to select the best QA approaches and mitigate potential damage.
- Responding to attacks — to analyze the committed attack and explore the ways to upgrade the system to exclude subsequent penetration.
- Recovering systems — to develop a response plan for potential breaches and sensitive data loss.
Advanced training on these and many other issues allows QA specialists to work with applications of any complexity, detect loopholes in advance and help release a reliable product.
Closing remark
Within highly sophisticated cyberattacks, companies are ready as never to pay greater attention to cybersecurity testing. It helps protect end-user personal data, minimize risks of cyber incidents, and make sure the software complies with cybersecurity requirements across the globe.
When looking for a QA provider to support you in that, ask some questions on testing methodologies, cyber incidents response plan, safety standards, internal security policy, and in-depth training.
If you’ve already made up your mind, feel free to reach out to a1qa’s experts to get holistic support on cybersecurity testing.








