OWASP as a guide to mobile apps security testing
Digital transformation paved the way for a faster transition to leveraging multiple devices. Now, smartphones are the most pervasive: end users harness mobile apps while performing day-to-day tasks and can no longer imagine the future without next-gen technologies.
This shift is streamlined even more due to the global situation, as more people have to move to online space to work, entertain, and savor communication from their homes.
Within the outbreak, the number of Internet users worldwide has dramatically increased. Statista survey indicates that 70% of respondents prefer mobile phones, compared with 40% of laptop users.
Therefore, companies rushed to build new applications, services, and systems. All of them include users’ sensitive data to one extent or another. Apps preventing coronavirus dissemination have appeared (for instance, people tracking service that warns of being at a risk zone was developed in China).
It’s vital to deliver robust and highly secure solutions, as cybercrimes are widespread now and will only increase in the future. Moreover, they adversely impact the budget. Recently the Ponemon Institute has finished a 14 years’ research showcasing that the most expensive data leak is detected in the U.S. And the average cost per breach has been increasing within years: from $3.54 million in 2006 to $8.19 million in 2019.
To avoid such unpleasant consequences, many organizations turn to OWASP standards being a trusted resource and providing an unbiased opinion reinforced by vast expertise. In this blog post, let’s discuss the most dangerous OWASP mobile top risks and show which steps to make to mitigate them.
Top 3 OWASP security issues in mobile applications
According to the NowSecure research, 85% of tested apps are vulnerable to at least one of OWASP mobile top 10 risks mentioned in the picture below, while nearly one-third of software products suffered from coding drawbacks.
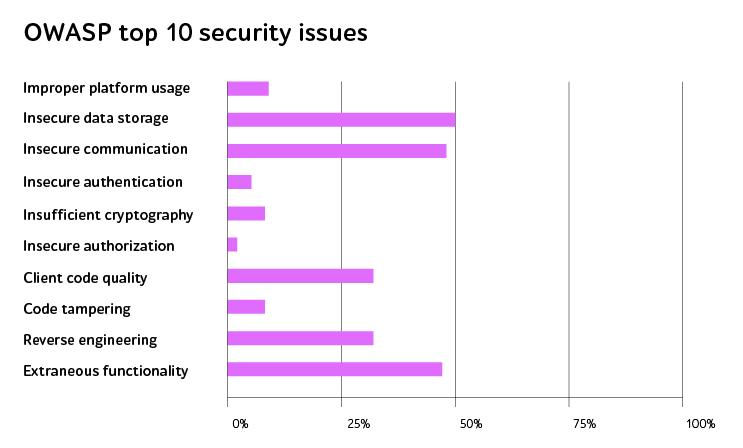
Let’s have a closer look at the top 3 challenges and shed light on why it’s essential to know about them.
1. Insecure storage of data
Bearing in mind that almost every application contains sensitive data like user credentials and private information, companies should provide an appropriate security level from both intentional and unintentional breaches.
And since there is a higher chance of physical theft or loss of mobile phone, rather than other devices, additional protections should be implemented to complicate retrieving the confidential information.
BFSI and healthcare are those industries that are exposed to the highest risk levels. No related company wants to see the spelled disaster with credit card numbers or details about health condition fall data into the wrong hands and get a distrust from the side of end users.
2. Unsafe network communication
Amid new technologies, the principle of open API is gaining more popularity in every economic sphere bringing benefits not only to companies but also to their clients. Interactions between services provide consumers with a multi-functional and user-friendly application while meeting planned business outcomes.
However, the risk of data leak through the communication channels between systems or remote service endpoints obstructs the further dissemination of this innovation.
Organizations should encrypt the transmitted data using TLS or SSL protocols with appropriate settings and make sure that connected third-party apps fit all verification requirements, including the minimum set of permissions, validation of input data from external sources, and much more.
3. Extraneous apps functionality
It came up that nearly 50% of assessed mobile applications have hidden functionality because of developers creating features that simplify software testing and debugging. In the future, they are likely to be in a production version which can be exploited by malicious users.
How does it work? Hackers effortlessly download the app, examine log and configurations files, and even the code itself, discovering vulnerabilities and extraneous features. Unauthorized users get access to the back end and can perform high-privileged actions, which may lead to revealing sensitive data, cryptographic constants, ciphers, and intellectual property.
It goes without saying that companies should consider this case and prevent their app from potential risks by ensuring high security level.
Elevating the mobile app soundness: 3 steps to make
How can a company create reliable software under tight deadlines?
Step 1. Implement security testing at all SDLC stages
According to the World Quality Report 2019-2020, over one in four respondents have optimized testing processes by introducing Agile methodologies. Once the company has introduced them, iterations become shorter with more frequent releases.
Security is of equal importance to deliver 360-degree safe, high-performance, user-friendly software solutions. So, try to build security testing from the initial steps relying on one of the key best practices to not test late in the SDLC when some vulnerabilities are overlooked and are cost-consuming to fix.
Solid test strategy, preliminary sensitive data identification, and building threat model compile the backbone of avoiding security issues in the future.
Step 2. Don’t bail on penetration testing
Application safety can also be evolved through penetration testing. Security testing specialists simulate the actions of real hackers, including spotting the vulnerabilities, exploiting them, and getting access to the necessary information.
Pentesting major perk is the search for particular loopholes required to achieve certain goals. The exploitation of vulnerabilities can lead to negative consequences in the form of a server crash or restart. So, ensure that you are ready for such responses.
Step 3. Automate more security testing
Automating security tests is another trend reflected in the WQR. Apart from achieving faster time-to-benefits, it reduces errors and increases test quality. More than 50% of respondents report that automation has decreased their overall security risk.
However, its full-fledged deployment is impossible as some actions are to be done manually. Nearly 30% of surveyed companies face challenges while balancing between these approaches.
Considering that each app has unique architecture, business logic, and technical peculiarities, various techniques and frameworks can be leveraged to verify its security.
In a nutshell
Within great demand for portable devices caused by the unstable situation, many companies kick-started building novel bespoke mobile solutions.
It’s vital to provide their security and high quality to lead in this ever-so-competitive market elevating end-users’ CX. It can be spoiled while facing pervasive security challenges like data storage, network communication, extraneous functionality, and more.
Harnessing OWASP security testing recommendations, businesses can easily overcome them. And a1qa – a grizzled QA vendor focused on testing the boundaries of what’s possible – can supervise the process to help you deliver upscale software solutions.
Have questions on security testing? Feel free to ask them to our experts.