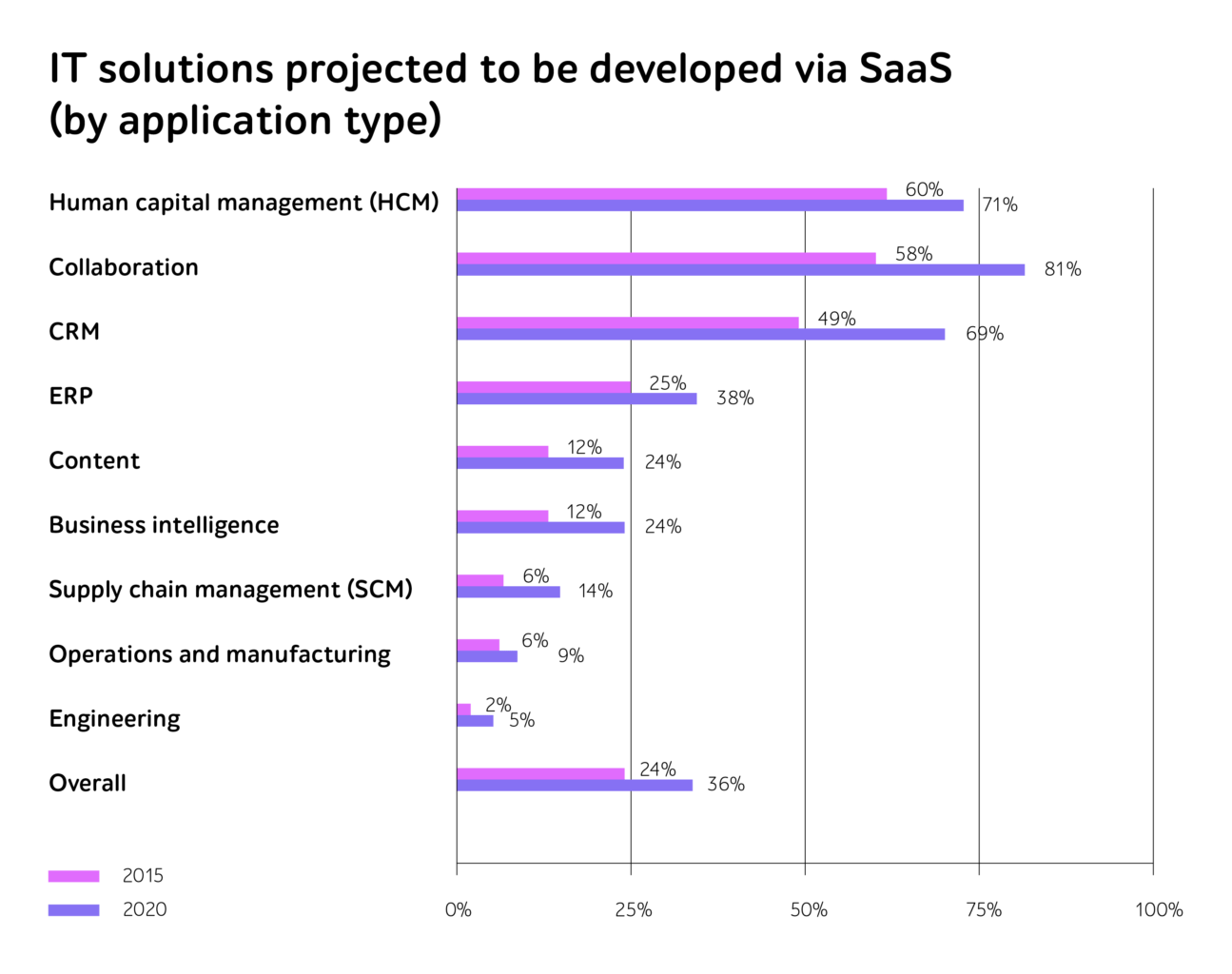
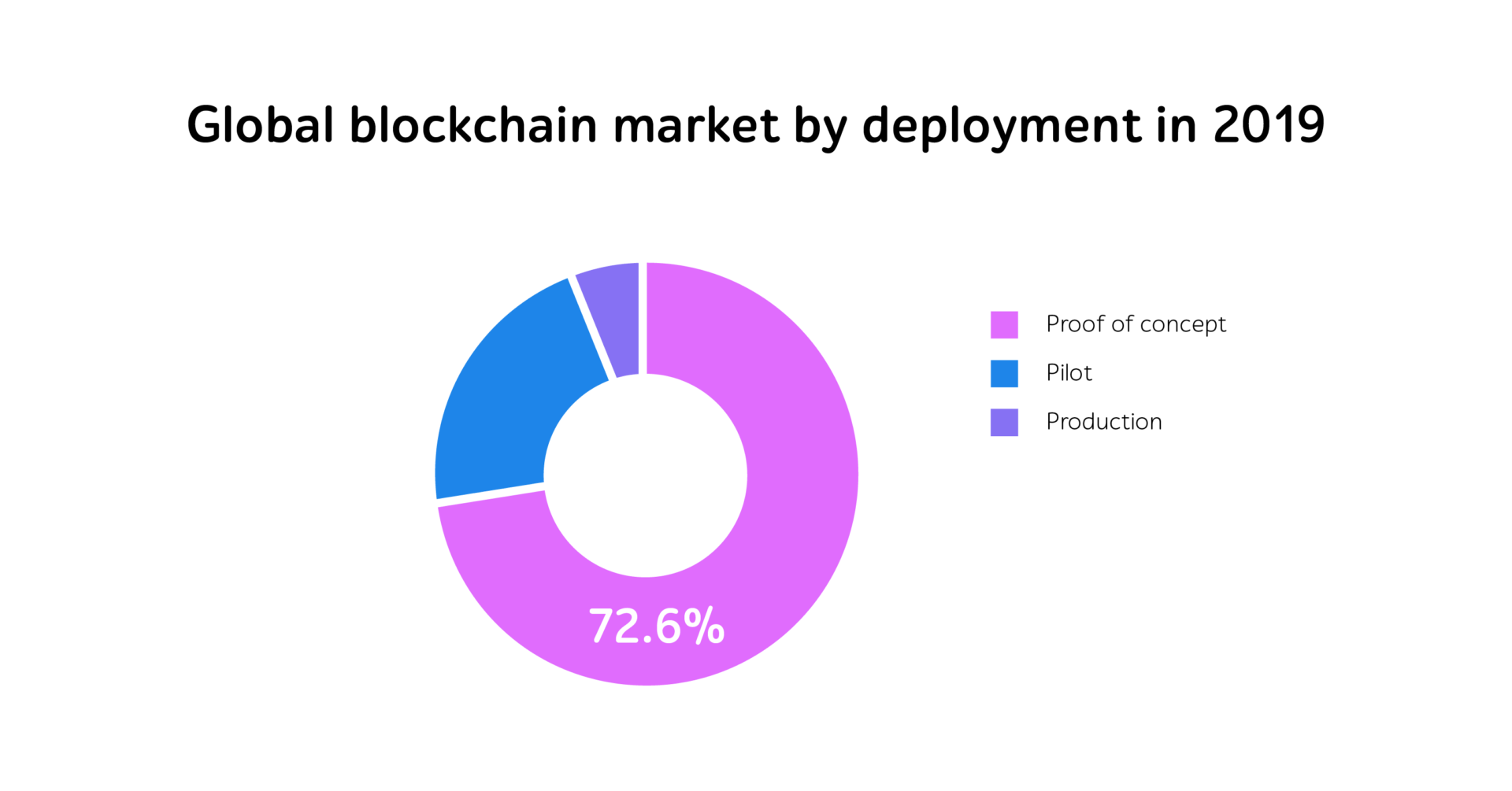
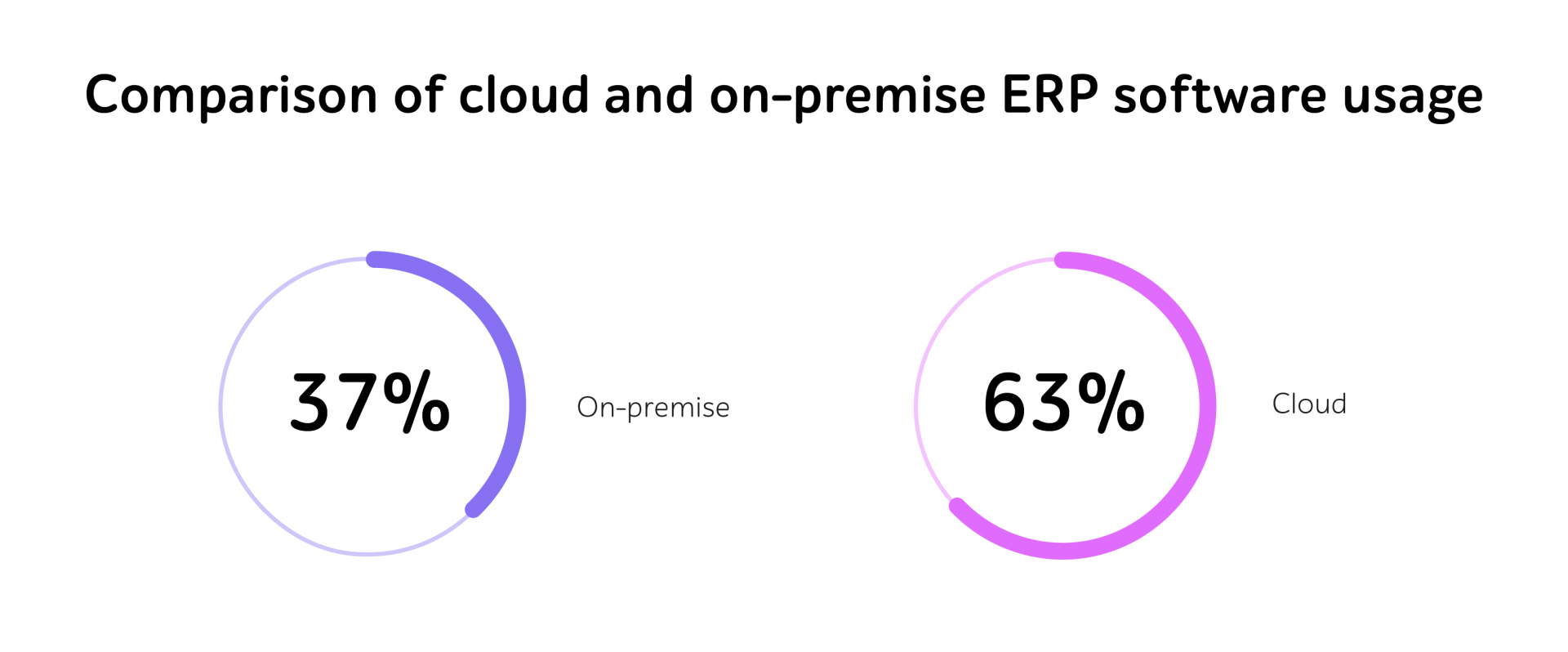
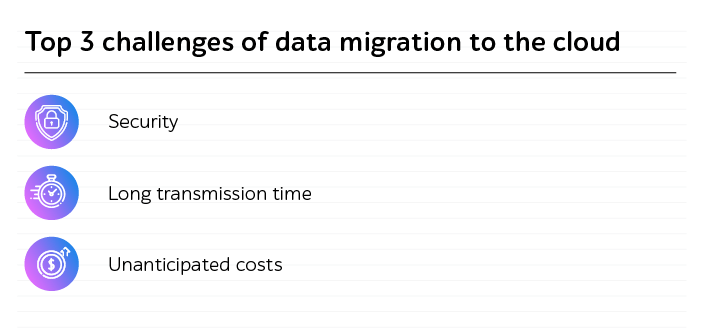
Microservices have emerged as the architectural blueprint for modern software development. They break down monoliths into agile, independently deployable components with their own logic, life cycle, and even tech stack. Allowing organizations to iterate faster, deploy independently, and scale specific features in isolation, they provide boosted speed and innovation. So, it’s not surprising that the experts of Research & Markets predict growth of microservices architecture market to $15.97 billion by 2029.
However, ensuring their flawless operation may be a challenging task. It demands a specialized QA approach that is decentralized, continuous, and deeply automated, as services can be updated independently and frequently, and their integration points can evolve at any time.
In this article, let’s explore specifics and setbacks of microservices-driven software as well as delve into a robust QA strategy for providing quality at scale.
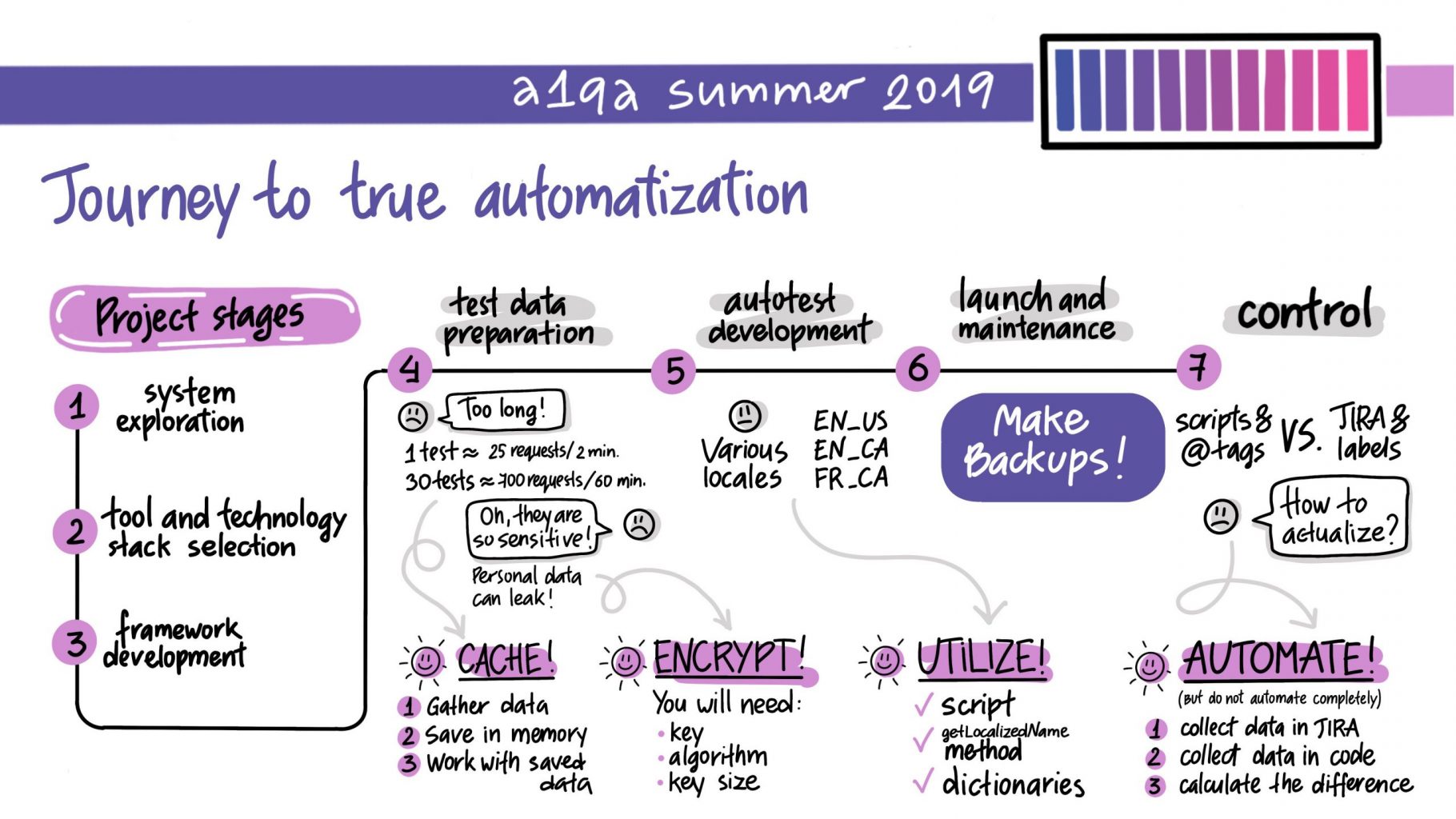
What is the concept behind microservices architecture?
Microservices architecture is a modern approach to software development in which a large application is built as a suite of autonomous services, each responsible for a particular business capability and operates independently, often with its own codebase, database, or deployment life cycle. These services usually communicate with one another over various protocols or asynchronous message queues.
This architectural model is fundamentally different from monolithic systems, where all features and functions are bundled into a single codebase. Microservices aim to improve scalability, speed up development cycles, enable decentralized ownership by teams, and reduce the risk of system-wide failures when making small, business-specific changes. Each service can be developed, tested, deployed, and scaled independently, allowing for greater organizational agility and faster advancement.
What risks come with designing applications using this approach?
Such systems have specific characteristics that introduce unique engineering and testing challenges that aren’t typically encountered in monolithic systems:
- Decentralized structure. These services are spread across different networks and environments (cloud, on-premises, or hybrid), meaning that issues like network latency, timeouts, or partial outages must be accounted for at all times.
- Mutual reliance. While each service is designed to be loosely coupled, they still rely on one another to deliver the expected user experience. It’s important to consider that an update in one service can introduce unexpected behavior in another.
- Language-diverse settings. Microservices often use different programming languages, frameworks, and data stores depending on the team or use case, leading to inconsistent tooling, monitoring gaps, and more complex test setups.
- On-the-fly scaling. Services in containerized environments (e.g., Kubernetes) can scale up or down at any time. This dynamic behavior introduces new classes of defects, such as race conditions during autoscaling events.
- Complex orchestration. With hundreds of microservices running independently, coordinating deployments, managing service dependencies, handling versioning, and ensuring reliable communication becomes a significant operational challenge.
- Security concerns. The distributed nature of microservices increases the attack surface with more endpoints and network traffic to protect. Additionally, ensuring all inter-service communication is encrypted and authenticated (e.g., via mTLS) adds complexity, while multiple APIs and services raise the risk of data exposure.
Within such a landscape, quality assurance serves as a structural pillar that supports the software’s integrity, rather than just a checkpoint at the end of development. It brings cohesion to a fragmented architecture, verifying that individual services continue to function reliably not only in isolation, but as part of a greater operational entity.
What QA verifications can power a resilient architecture?
Let’s have a look at indispensable QA verifications that can help guarantee the software remains robust under pressure, adaptable in the face of change, and reliable at scale.
Performance testing
Unlike a monolith where internal calls are fast and reliable, microservices often communicate over a network, which introduces latency, potential failure points, and dependencies on external systems such as databases or third-party APIs. That’s why performance testing plays a pivotal role in identifying these weaknesses, ensuring that each service and the system as a whole can operate efficiently under varying levels of real-world or extreme conditions.
With a full spectrum of performance testing services, QA engineers measure response times, ensuring that services reply within acceptable intervals, even as the number of concurrent users increases. Equally important is evaluating how services interact with one another, whether delays in one service propagate to others or remain isolated. Special attention is given to bottlenecks in API gateways, databases, and message queues, where long queue durations can significantly increase response times. Resource usage is also scrutinized, as inefficient CPU or memory consumption can lead to degraded performance or service crashes.
Contract testing
Within microservices architecture, each service is intended to be autonomous. However, this independence creates the risk of integration mismatches when one service consumes another’s API. Contract testing mitigates this risk by defining and enforcing interaction of contracts between service consumers and providers. These contracts describe the structure and semantics of the exchanged messages and help verify that services fulfill mutual expectations.
Therefore, QA engineers validate contracts from both sides, thus significantly reducing the likelihood of integration failures after deployment and supporting the continuous delivery of individual services.
Security testing
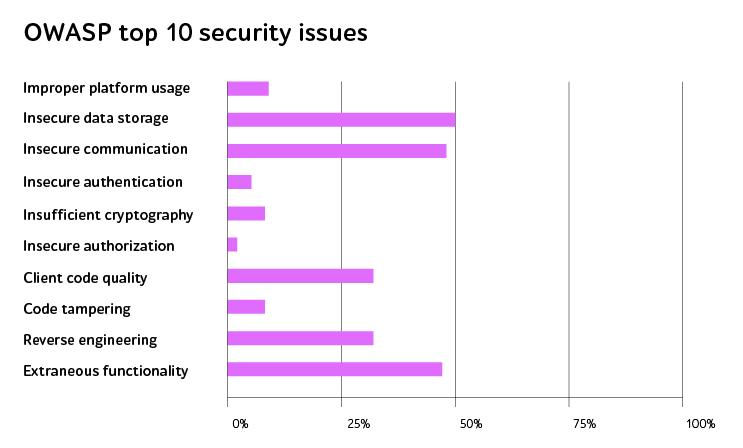
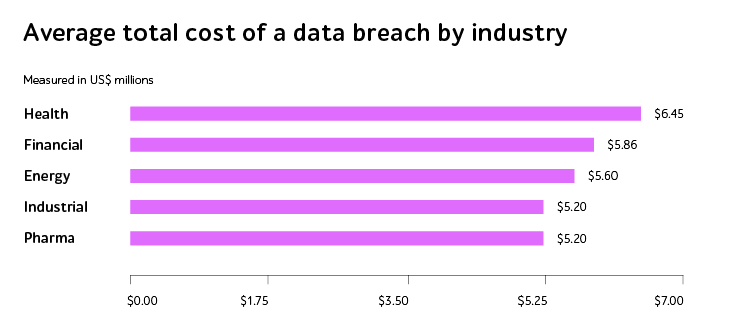
Security testing of microservices should become another critical aspect, ensuring that the distributed components of an IT product are safe and have no weaknesses in API authentication and authorization mechanisms, data validation, communication protocols, and other vital functionalities.
By relying on rigorous vulnerability scanning, penetration testing, and risk assessment, QA engineers look for improper access controls, broken authentication logic, injection vulnerabilities and verify that sensitive data is adequately protected even when transferred between internal modules. This ensures the resilience and readiness of microservices in the face of real-world threats.
Component testing
As microservices architecture splits an application into independently deployable services, it’s essential to test each component in isolation to ensure that the behavior of one microservice is predictable, reliable and confirm that it performs its tasks as expected without depending on other services.
In the scope of component testing, QA engineers verify input and output data formats, response codes, error handling routines, and any local data storage mechanisms, detecting issues early before they propagate through interconnected systems. Additionally, they also test the core function of the module itself. For example, if it’s a reporting unit, its logic and output accuracy must be validated. Specialists also simulate real-world interactions at the boundary of the service using stubs or mocks to replicate external dependencies, focusing solely on the internal correctness of the microservice.
Automated testing
Test automation can become a valuable addition to a QA process, as it provides the speed and accuracy required to continuously validate numerous independent services across development cycles. In environments where deployments occur frequently, automated tests ensure that existing services remain unaffected by changes in adjacent components.
Therefore, QA automation engineers develop and maintain automated test suites, often running them in containerized environments that mimic real deployment conditions. These tests are integrated into CI/CD pipelines to provide continuous feedback, helping teams detect issues early, speed up release cycles, maintain system stability, and reduce costs.
For instance, to help the developer of online mobile games created based on a microservices architecture rectify software glitches, a1qa defined test automation scope, built Java-based automation suites, created a bespoke framework, integrated Allure Report to enhance traceability and oversight of test cases, and strengthened the process with AI. These strategic efforts ensured bugless software operation and saved 788 hours of manual testing in just 9 months.
End-to-end testing
End-to-end testing ensures that the entire system functions as expected from the user’s perspective, validating the flow across all microservices. Because these services are independently deployed, changes in one can unintentionally affect others. Therefore, testing should be continuous, helping catch integration issues early and maintaining a consistent, reliable user experience.
During this activity, QA engineers simulate real-world user scenarios that span multiple services and interfaces, testing not only correctness of data being passed between services but also ensuring the system behaves correctly under various conditions. For example, during testing an eCommerce solution specialists check that placing an order correctly triggers other related services. This full-cycle validation is crucial to detect issues like broken service dependencies or communication failures that could otherwise go unnoticed during isolated service testing.
Integration testing
In microservices architectures, the complexity of inter-service communication requires rigorous integration testing to ensure overall system stability. While individual units may function correctly in isolation, their interactions can expose critical defects only visible when services work together.
That’s why while performing integration testing, QA specialists replicate actual production scenarios, examine the behavior of APIs, message queues, databases, and other shared resources. They validate that services correctly parse inputs, handle failures, and strictly follow service contracts.
In a nutshell
Microservices demand a testing strategy that ensures every service runs in harmony. By blending robust test automation with functional and non-functional testing services, project teams can not only meet the challenges of microservices architecture but build systems that withstand failure and evolve with confidence.